Ip address blocking service.
While experimenting with hosting options I tried an Amazon Cloud virtual machine among others to test hosting performance and ease of setting up Drupal on Windows compared to Linux shared hosting I use usually. Familiar Windows environment was pleasantly easy to configure, but failed to impress with server performance. After thorough disk space cleanup and uninstalling of extra applications I stumbled upon Event Log records of Brute Force attack attempts (Event Id 4625) that look similar to:
An account failed to log on. Subject: Security ID: SYSTEM Account Name: IP-0AE0771F$ Account Domain: WORKGROUP Logon ID: 0x3e7 Logon Type: 10 Account For Which Logon Failed: Security ID: NULL SID Account Name: david Account Domain: IP-0AE0771F Failure Information: Failure Reason: Unknown user name or bad password. Status: 0xc000006d Sub Status: 0xc0000064 Process Information: Caller Process ID: 0x580 Caller Process Name: C:\Windows\System32\winlogon.exe Network Information: Workstation Name: IP-0AE0771F Source Network Address: 50.97.3.27 Source Port: 1293 Detailed Authentication Information: Logon Process: User32 Authentication Package: Negotiate Transited Services: - Package Name (NTLM only): - Key Length: 0 This event is generated when a logon request fails. It is generated on the computer where access was attempted. ...
From different ip addresses multiple times per second someone tried to guess administrator's password (or another privileged user's like david in the example above) which had an utterly negative impact on web server response. Having failed to quickly find an easy and free way to counter such attacks I decided to write a simple service myself that would work as follows:
- Scan Security Event Log for 4625 event;
- Extract ip address from event details;
- Check event log for multiple failed logon attempts from this ip address within short timeframe;
- Add a rule to Windows Firewall denying access from this ip;
- Wait specified time and unblock offending ip - blocking for an hour usually more than enough to deter attacker while unblocking should cater for users behind provider proxy using the same ip address.
Field testing shown excellent results - downtime caused by brute force attacks ceased to exist. If you could benefit from such a service you are welcome to use it - free of charge for any purpose, commercial, residential, recreational or otherwise (reference to this site required with any distribution), but please remember to set strong password for your admin account. It requires .Net 4 Framework to work and two steps to install:
- Unpack attached zip file to a folder on your hard drive (for example into "C:\Program Files (x86)\IpBlock\");
- Run "C:\Program Files (x86)\IpBlock\ipblock.exe - install" from the command line
Uninstall is just one step:
C:\Program Files (x86)\IpBlock\ipblock.exe - uninstall
You could monitor the progress in Event Log:
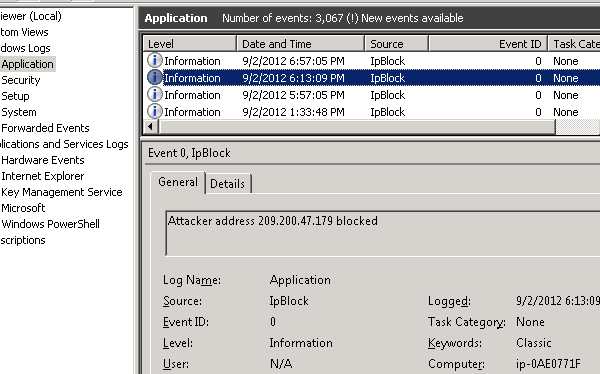
Those who love to peek at the source code could do so at https://bitbucket.org/ssshuler/ipblock. Please forward your comments and suggestions to the author, he'll pickle them and save for times of famine.
